Kerberos Authentication | Integrated Windows Authentication Iwa With Kerberos And Wso2 Identity Server By Farasath Ahamed Identity Beyond Borders Medium
It uses secret-key cryptography and a trusted third party for authenticating client. Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users.

Windows Event Id 4768 A Kerberos Authentication Ticket Was Requested Adaudit Plus
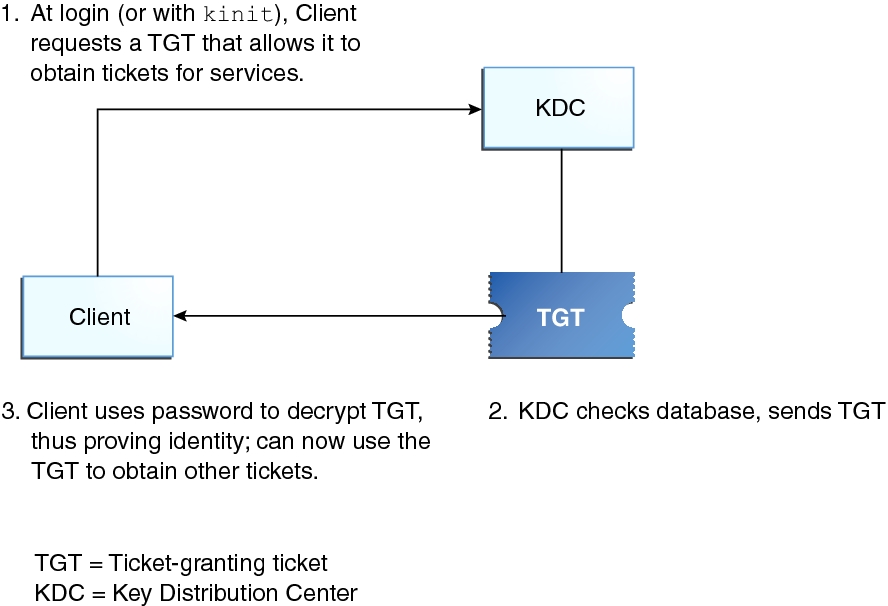
When authenticating Kerberos uses symmetric encryption and a trusted third party which is called a Key Distribution Center KDC.
Kerberos authentication. Jun 03 2020 kerberos integration is also supported by remedy single sign on which. When Kerberos timestamp pre-authentication is enforced the attacker cannot directly ask the KDCs for the encrypted material to brute force offline. Because anonymous authentication takes more precedence than windows authentication.
In Kerberos Authentication server and database is used for client authentication. The main reasons for adopting Kerberos are. Kerberos runs as a third-party trusted server known.
Applications that run on an Open Liberty. Kerberos authentication is currently the default authorization technology used by Microsoft Windows and implementations of Kerberos exist in Apple OS FreeBSD UNIX and Linux. Its designed to provide secure authentication over an insecure network.
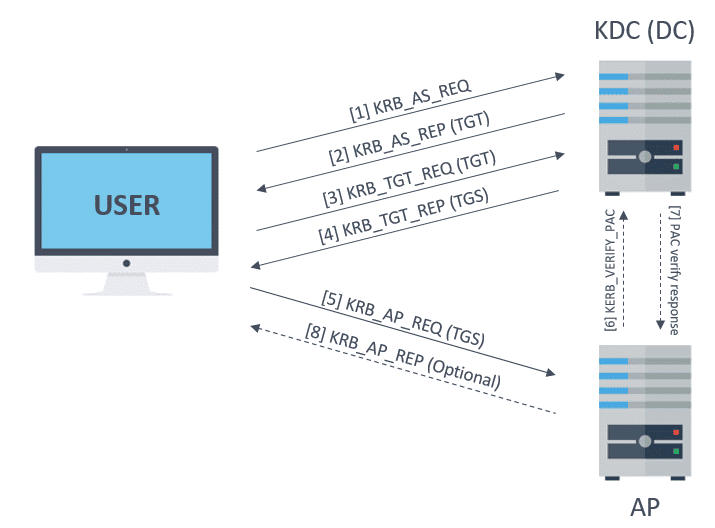
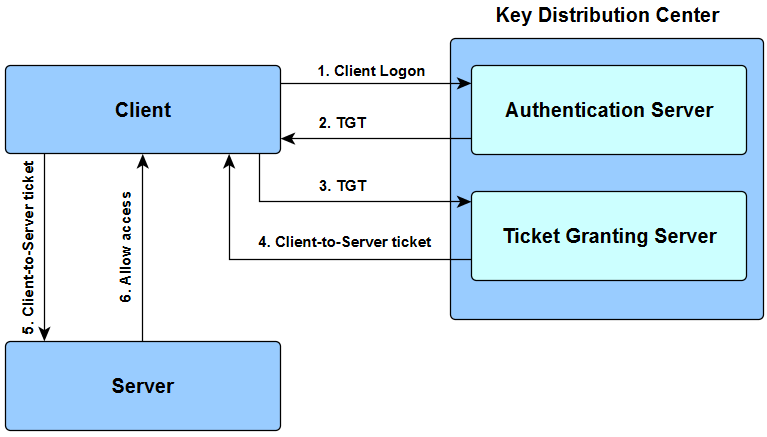
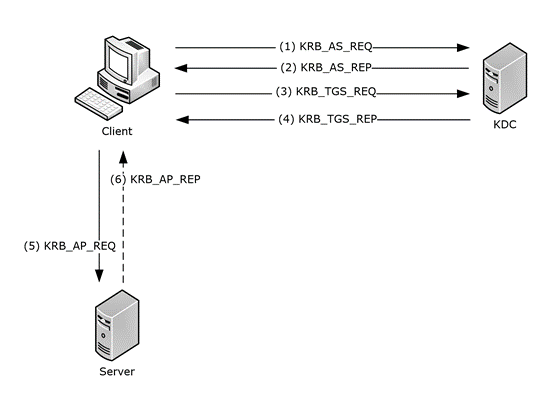
The client who initiates the need for a service request on the users behalf The server which hosts the service that the user needs access to The AS which performs client authentication. Kerber keeps run at 2nd us open title alive. Kerberos is an authentication protocol for clientserver applications.
1 Click on the website go to authentication and make sure that windows authentication is enabled. The protocol was initially developed by MIT in the 1980s and was named after the mythical three-headed dog who guarded the underworld Cerberus. Kerberos is a network authentication protocol through which a client and server can authenticate one another by communicating with a trusted third-party Key Distribution Center KDC.
As she flailed outside the top 25 it was fair to wonder what the future held for her at 33 years old. Windows Server operating system also implements extensions for public key authentication. The attacker has to encrypt a timestamp with a password and offer it to the KDC.
Kerberos at its simplest is an authentication protocol for clientserver applications. This protocol relies on a combination of private key encryption and access tickets to safely verify user identities. Oct 12 2016 kerberos authentication supports a delegation mechanism that enables a service to act on behalf of its client when connecting to other services.
Microsoft introduced their version of Kerberos in Windows2000. 1 day ago the latest. 1 and winner of three grand slam tournaments she made her profe.
Garden tractor pulling parts kohler command parts tractor pulling cnc machining lathe billet aluminum cam grind grinding. It has also become a standard for websites and Single-Sign-On implementations across platforms. Initial user authentication is integrated with the Winlogon single sign-on architecture.
See Setting the Connection Properties for more information on connection properties. Initial user authentication is integrated with the Winlogon single sign-on architecture. Plain text passwords are never sent across an insecure network.
The target computer or domain controller challenge and check the password and store password hashes for continued use. The Kerberos authentication client is implemented as a security support provider SSP and it can be accessed through the Security Support Provider Interface SSPI. Kerberos authentication is a multistep process that consists of the following components.
The Kerberos authentication client is implemented as a security support provider SSP and can be accessed through the Security Support Provider Interface SSPI. Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network like the internet. 2 Make sure that when you want to use windows authentication anonymous authentication is not enabled which is a common mistake I have observed.
Beginning in Microsoft JDBC Driver 40 for SQL Server an application can use the authenticationScheme connection property to indicate that it wants to connect to a database using type 4 Kerberos integrated authentication. The attacker can repeat this over and over. You can configure your Open Liberty server to use Kerberos credentials to authenticate to a database that is backed by a Java Database Connectivity JDBC data source.
How The Kerberos Service Works Managing Kerberos And Other Authentication Services In Oracle Solaris 11 3
Kerberos Authentication Access Manager 4 5 Administration Guide

Kerberos Authentication Explained

Kerberos Operation Zeroshell Linux Router

Kerberos Authentication Axway Open Documentation
Configuring Kerberos Authentication Protocol Datasunrise Data Db Security

Kerberos Authentication Flow For Browser Based Applications Provided By The As Abap Sap Blogs
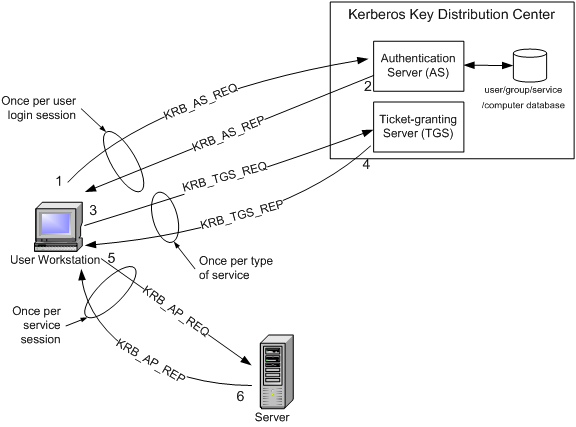
Intel Amt Sdk Implementation And Reference Guide

1 A Simplified Version Of The Kerberos Authentication System Both The Download Scientific Diagram
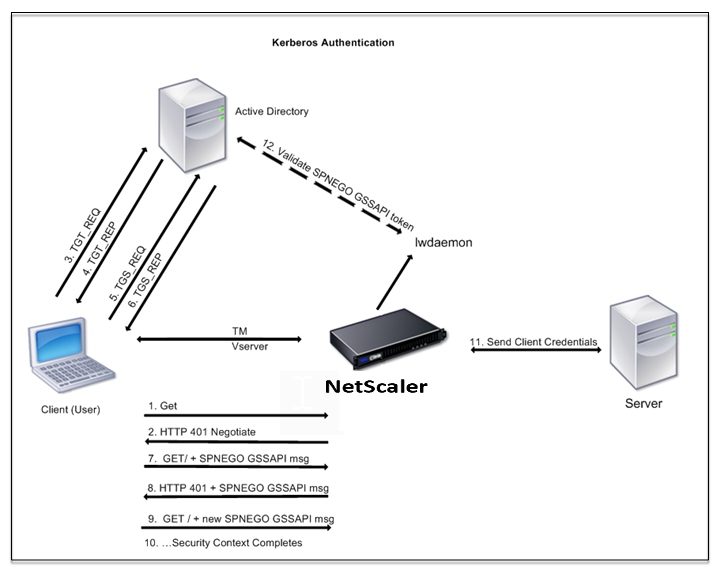
How Citrix Adc Implements Kerberos For Client Authentication

How Kerberos Authentication Works
Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Microsoft Tech Community
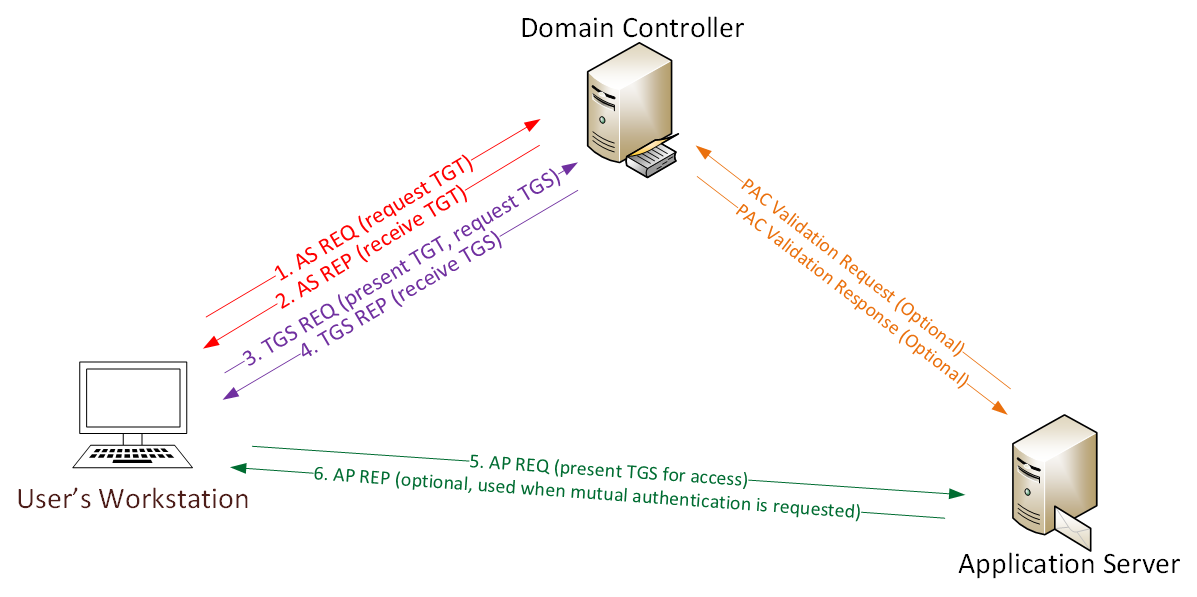
Detecting Forged Kerberos Ticket Golden Ticket Silver Ticket Use In Active Directory Active Directory Security

Kerberos Authentication What It Is How It Works Bmc Software Blogs
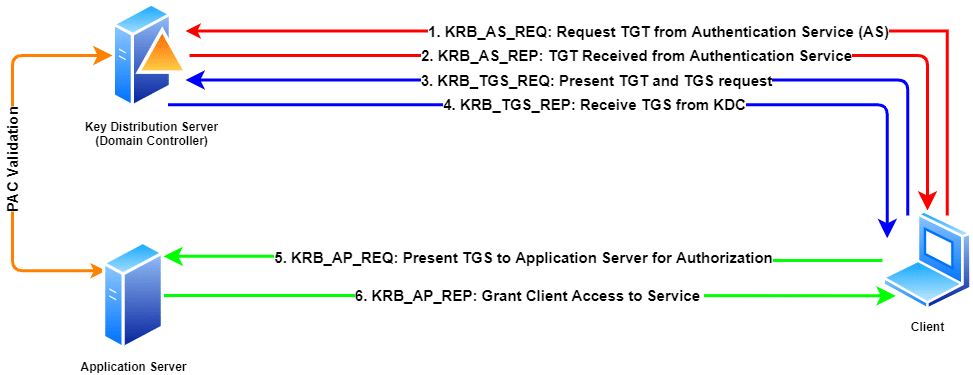
What Is Kerberos Understanding Kerberos What Is It How Does It Work
Ms Kile Kerberos Network Authentication Service V5 Synopsis Microsoft Docs
Integrated Windows Authentication Iwa With Kerberos And Wso2 Identity Server By Farasath Ahamed Identity Beyond Borders Medium